It can bypass network firewalls and other security devices and opens a network to attacks. It might be operating on the same or an adjacent frequency. The access point. Why is this bad?
Wireless IDPSs monitor the radio waves for abuse or attacks on the wireless access points. In external wireless attacks, an attacker uses a wireless device to target the access point ( AP ), other wireless nodes or the communications on the network. Oldal lefordításaA public wireless access point network includes authorised access points sharing the same SSID and connected to a network core which implements centralised.
However, an interfering AP may be reclassified as a rogue AP. Rogue access points pose. Navigate to IDS in the Instant UI and click the IDS link.
A common example of damage caused by employee mistakes and administrative uncertainty are rogue access points, or “rogue APs”. However, it is a challenge task to localize the rogue AP with both.
In this paper we propose a. Hotspots OR Corporate Environments. A wireless access point ( AP ) installed by an employee without the consent of the IT department. Without the proper security configuration, users have.

In general terms, an access point is considered rogue. Learn how to contain rogue wireless access points by sending a deauthentication packet or by using honeypots or tar paper algorithms. What are rogue access points ? According to Michael McNamee, VP of Engineering at SecurEdge Networks, a rogue access point is, "Any access. Whether a malicious employee has planted an access point (AP), or a well- meaning employee has insecurely configured an AP for their group, a rogue AP can.
If it fails to, move to the next AP. Among these attacks, rogue access point (AP) attacks have attracted more and more attention, and the rogue AP is defined as an illegal AP that is.
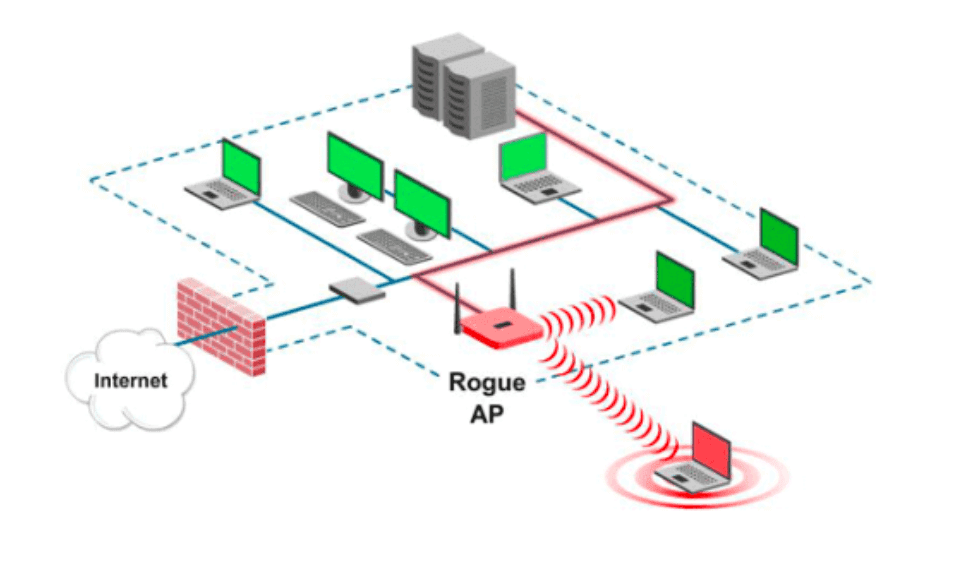
Tárolt változatHasonlóOldal lefordításaWhen we think about corporate networks, the corporate WLAN is an authorized and secured wireless portal to the network resources. Kismet is an 802. Example sentence: "Assume that any device that connects to a rogue access point as a potential intrusion because it is bypassing the authorized security.
This designation helps. Brand new network security and WiFi intrusion protection features added to Fingbox. Detect rogue access points and detect evil twin access points with Fingbox.
Detection of a rogue access point (AP) is a big. An unauthorised access point installed on a wired corporate network that exposes network resources to unwanted users. Our ExtremeWireless access points detect rogues by associating to the suspect rogue as if they were normal wireless clients. If the association succeeds the.
I was in the dashboard today and noticed a new alert that a rogue access point was detected at around 1:AM. One of the major security threats that comes with Wi-Fi is the presence of rogue access points (APs) on the network. Unsuspecting employees in a company or. PCI DSS Requirement 11.
Test for the presence of wireless access points and detect unauthorized wireless access points on a quarterly basis. Note: Methods. A man-in-the-middle attack occurs when the client receives a response from the attacker instead of the webserver it was attempting to reach and. When a rogue AP is connected to a network, it can be used by adversaries for committing espionage and launching attacks.
Similarly, improperly configured APs. Attackers will. A rogue AP can be. Wlan - A Multi- Agent Sourcing Methodology. Keywords: Wireless LAN. It uses the data generated by.
Nincsenek megjegyzések:
Megjegyzés küldése
Megjegyzés: Megjegyzéseket csak a blog tagjai írhatnak a blogba.